identity encryption 2025-10-28T06:49:59Z
-
 Identity VIdentity V is an asymmetrical horror mobile game developed by NetEase, designed for Android devices. This game offers an engaging experience where players can immerse themselves in a gothic art style and mysterious narrative. Players can download Identity V to engage in thrilling 1 vs. 4 gameplay, where one player takes on the role of a hunter while the other four assume the role of survivors.In Identity V, the gameplay revolves around intense combat scenarios. Survivors must work coop
Identity VIdentity V is an asymmetrical horror mobile game developed by NetEase, designed for Android devices. This game offers an engaging experience where players can immerse themselves in a gothic art style and mysterious narrative. Players can download Identity V to engage in thrilling 1 vs. 4 gameplay, where one player takes on the role of a hunter while the other four assume the role of survivors.In Identity V, the gameplay revolves around intense combat scenarios. Survivors must work coop -
 CyberArk IdentityCyberArk Identity is a mobile application designed to provide users with secure access to organizational applications and resources on Android devices. This app is also known for its functionality in facilitating single sign-on (SSO) access, which allows users to log into multiple c
CyberArk IdentityCyberArk Identity is a mobile application designed to provide users with secure access to organizational applications and resources on Android devices. This app is also known for its functionality in facilitating single sign-on (SSO) access, which allows users to log into multiple c -
 The glow of my laptop screen felt like an interrogation lamp that night. I'd been chasing a data breach trace for hours, sweat trickling down my neck as I realized my usual email client had been silently broadcasting my search patterns. That's when I remembered the Swiss invitation buried in my spam folder weeks earlier - some privacy-focused service called Infomaniak. Desperation makes you try things you'd normally ignore.
The glow of my laptop screen felt like an interrogation lamp that night. I'd been chasing a data breach trace for hours, sweat trickling down my neck as I realized my usual email client had been silently broadcasting my search patterns. That's when I remembered the Swiss invitation buried in my spam folder weeks earlier - some privacy-focused service called Infomaniak. Desperation makes you try things you'd normally ignore. -
 Microsoft Identity PassIdentity Pass is a Microsoft application for processing access requests to organizational resources. When you submit a request, biometric data is collected. A live photo is taken and compared with your employee badge photo. Biometric data will be stored for one year. You may n
Microsoft Identity PassIdentity Pass is a Microsoft application for processing access requests to organizational resources. When you submit a request, biometric data is collected. A live photo is taken and compared with your employee badge photo. Biometric data will be stored for one year. You may n -
 iDenfy Identity VerificationIDenfy goal is to turn your customer\xe2\x80\x99s smart-phone (iOS and Android) or computer into an ID scanning terminal that makes it fast and easy to capture and verify their ID and other credentials to meet KYC requirements. Real-time ID scanning and verification is ap
iDenfy Identity VerificationIDenfy goal is to turn your customer\xe2\x80\x99s smart-phone (iOS and Android) or computer into an ID scanning terminal that makes it fast and easy to capture and verify their ID and other credentials to meet KYC requirements. Real-time ID scanning and verification is ap -
 AES Encryption (256-Bit)Encryption is a way of protecting your files with a password. This application encrypts your files using 256-Bit AES Encryption Protocol so it would take someone using a brute force attack around "2.29*10^32 years" to unlock your file. In short, it's one of the best encryptions out there.With this app, you can encrypt your files in these simple steps.- Choose a file or multiple files at once- Enter a password- Wait for the encryption/decryption to complete- Your files wil
AES Encryption (256-Bit)Encryption is a way of protecting your files with a password. This application encrypts your files using 256-Bit AES Encryption Protocol so it would take someone using a brute force attack around "2.29*10^32 years" to unlock your file. In short, it's one of the best encryptions out there.With this app, you can encrypt your files in these simple steps.- Choose a file or multiple files at once- Enter a password- Wait for the encryption/decryption to complete- Your files wil -
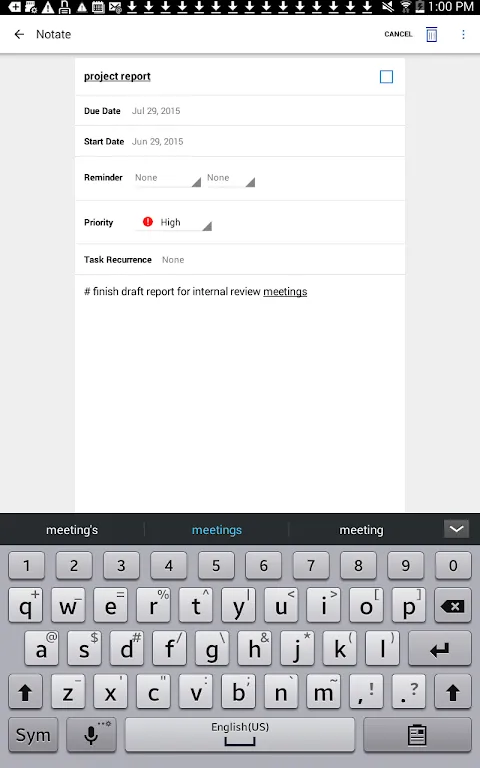 Rain lashed against the lodge windows like angry spirits as I stared at the financial projections glowing on my BlackBerry. Three hours from civilization, with only a dying generator humming in protest against the storm, and I'd just spotted the lethal typo - a misplaced decimal point that could vaporize our startup's valuation. My fingers trembled not from the alpine chill seeping through log walls, but from the realization that our entire funding round balanced on editing this cursed PDF befor
Rain lashed against the lodge windows like angry spirits as I stared at the financial projections glowing on my BlackBerry. Three hours from civilization, with only a dying generator humming in protest against the storm, and I'd just spotted the lethal typo - a misplaced decimal point that could vaporize our startup's valuation. My fingers trembled not from the alpine chill seeping through log walls, but from the realization that our entire funding round balanced on editing this cursed PDF befor -
 SSE - File & Text EncryptionSecret Space Encryptor (S.S.E.)File Encryption, Text Encryption and Password Manager applications integrated into the all-in-one solution. Important Introductory Note:This application provides many options and is intended for experienced users. All data are really encrypted (mathematically altered) using keys derived from your password. If you forget the password, your data is lost no matter how many vulgar insults you send to our e-mail. The correct password is the o
SSE - File & Text EncryptionSecret Space Encryptor (S.S.E.)File Encryption, Text Encryption and Password Manager applications integrated into the all-in-one solution. Important Introductory Note:This application provides many options and is intended for experienced users. All data are really encrypted (mathematically altered) using keys derived from your password. If you forget the password, your data is lost no matter how many vulgar insults you send to our e-mail. The correct password is the o -
 eScription OneeScription One allows authorized clinicians to create and manage high quality documentation for an EMR with minimal time and effort. Clinicians dictate the narrative and keep pace with busy patient loads without compromising time with patients, revenue potential or length of workday. Meanwhile, timely, complete, structured data in the EMR reduces claim rejections, decreases time to bill and enhances compliance.A real-time schedule feed serves as a daily work list while access to pa
eScription OneeScription One allows authorized clinicians to create and manage high quality documentation for an EMR with minimal time and effort. Clinicians dictate the narrative and keep pace with busy patient loads without compromising time with patients, revenue potential or length of workday. Meanwhile, timely, complete, structured data in the EMR reduces claim rejections, decreases time to bill and enhances compliance.A real-time schedule feed serves as a daily work list while access to pa -
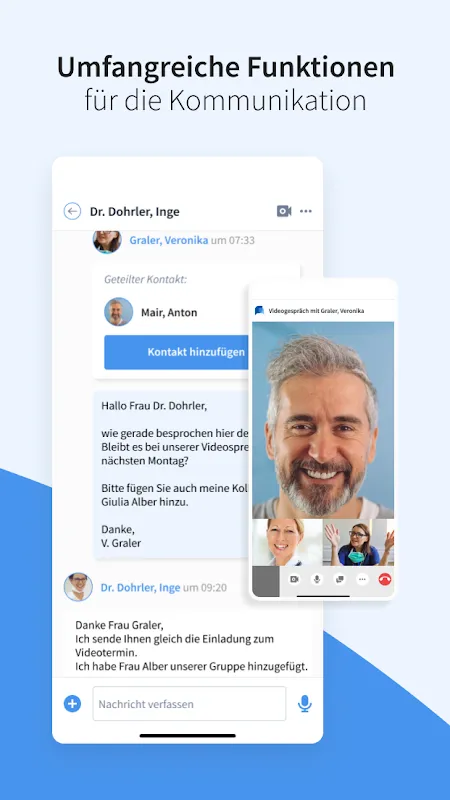 Rain lashed against the window as I stared at the glucose monitor's blinking red numbers - 387 mg/dL. Midnight. Alone. That familiar metallic taste of panic flooded my mouth as I fumbled for my endocrinologist's after-hours number. Three rings. Voicemail. Again. My trembling fingers left a sweaty smear on the phone screen when Sarah's text suddenly appeared: "Download that healthcare comms thingy yet? Screenshot attached." The logo glared back: a blue shield with a white heartbeat line. Last res
Rain lashed against the window as I stared at the glucose monitor's blinking red numbers - 387 mg/dL. Midnight. Alone. That familiar metallic taste of panic flooded my mouth as I fumbled for my endocrinologist's after-hours number. Three rings. Voicemail. Again. My trembling fingers left a sweaty smear on the phone screen when Sarah's text suddenly appeared: "Download that healthcare comms thingy yet? Screenshot attached." The logo glared back: a blue shield with a white heartbeat line. Last res -
 Rain lashed against the hotel window in Prague as I stared at the encrypted email confirmation, fingers trembling. The client's prototype schematics sat in my cloud drive – blueprints that could bankrupt my firm if intercepted. Earlier that morning, a panicked call from headquarters revealed our usual file transfer service had been compromised; competitors were circling like sharks. My throat tightened with every notification ping. That's when I remembered the unassuming icon buried in my apps f
Rain lashed against the hotel window in Prague as I stared at the encrypted email confirmation, fingers trembling. The client's prototype schematics sat in my cloud drive – blueprints that could bankrupt my firm if intercepted. Earlier that morning, a panicked call from headquarters revealed our usual file transfer service had been compromised; competitors were circling like sharks. My throat tightened with every notification ping. That's when I remembered the unassuming icon buried in my apps f -
 Sweat pooled beneath my collar as the phone rang for the seventh consecutive morning. That infuriating robotic hold music had become the soundtrack to my tachycardia - a cruel joke reminding me how my own pulse mocked me while specialists remained untouchable. Each dropped call felt like betrayal; each voicemail a black hole swallowing my panic. My cardiologist's office might as well have been on Mars. Then came Tuesday's tuna salad lunch with Sarah, who watched me stab lettuce like it owed me m
Sweat pooled beneath my collar as the phone rang for the seventh consecutive morning. That infuriating robotic hold music had become the soundtrack to my tachycardia - a cruel joke reminding me how my own pulse mocked me while specialists remained untouchable. Each dropped call felt like betrayal; each voicemail a black hole swallowing my panic. My cardiologist's office might as well have been on Mars. Then came Tuesday's tuna salad lunch with Sarah, who watched me stab lettuce like it owed me m -
 That damned static lock screen haunted me every morning. For eight months, I'd wake to the same lifeless geometric pattern - a corporate ghost haunting my personal device. My thumb would instinctively stab at the screen, triggering that hollow *click* sound that echoed the emptiness of my digital existence. Then came the Tuesday commute disaster: fumbling with my phone in the rain, I missed my train because I couldn't quickly access notifications through that monolithic wall of pixels. That even
That damned static lock screen haunted me every morning. For eight months, I'd wake to the same lifeless geometric pattern - a corporate ghost haunting my personal device. My thumb would instinctively stab at the screen, triggering that hollow *click* sound that echoed the emptiness of my digital existence. Then came the Tuesday commute disaster: fumbling with my phone in the rain, I missed my train because I couldn't quickly access notifications through that monolithic wall of pixels. That even -
 Monday morning chaos hit like a monsoon rain - daycare alerts bleeding into client demands while dating app notifications flashed like emergency flares. My single phone number had become a digital warzone where diaper updates collided with corporate jargon. I remember trembling fingers scrolling through that mess during a board meeting, desperately muting my phone as a preschool notification blared "potty accident emergency" through the speaker. The humiliation burned hotter than coffee spilled
Monday morning chaos hit like a monsoon rain - daycare alerts bleeding into client demands while dating app notifications flashed like emergency flares. My single phone number had become a digital warzone where diaper updates collided with corporate jargon. I remember trembling fingers scrolling through that mess during a board meeting, desperately muting my phone as a preschool notification blared "potty accident emergency" through the speaker. The humiliation burned hotter than coffee spilled -
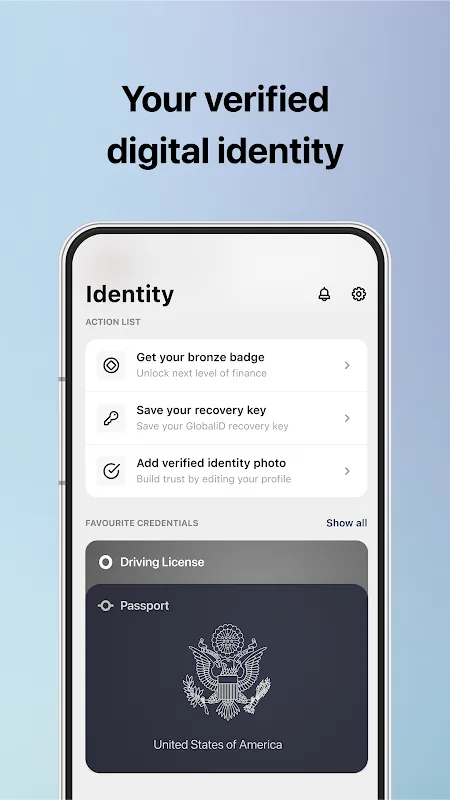 Rain lashed against the skyscraper windows as I paced the marble floor of the investment firm's lobby, my dress shoes squeaking with each nervous turn. Fifteen minutes until my pitch meeting - the culmination of six months of work - and I realized with gut-wrenching clarity that my physical ID wallet lay forgotten on my kitchen counter. Security wouldn't budge without verification. "No identification, no entry," the stone-faced guard repeated, his hand resting on the biometric scanner. My career
Rain lashed against the skyscraper windows as I paced the marble floor of the investment firm's lobby, my dress shoes squeaking with each nervous turn. Fifteen minutes until my pitch meeting - the culmination of six months of work - and I realized with gut-wrenching clarity that my physical ID wallet lay forgotten on my kitchen counter. Security wouldn't budge without verification. "No identification, no entry," the stone-faced guard repeated, his hand resting on the biometric scanner. My career -
 Staring at the blank Zoom background before my keynote at the Global Heritage Symposium, panic clawed at my throat. How could I represent centuries of cultural legacy when my own reflection screamed "generic corporate drone"? My grandmother's stories of silk turbans whispering royal secrets felt galaxies away from this pixelated purgatory. Then I remembered that quirky app icon – a jeweled crown hovering over a smartphone.
Staring at the blank Zoom background before my keynote at the Global Heritage Symposium, panic clawed at my throat. How could I represent centuries of cultural legacy when my own reflection screamed "generic corporate drone"? My grandmother's stories of silk turbans whispering royal secrets felt galaxies away from this pixelated purgatory. Then I remembered that quirky app icon – a jeweled crown hovering over a smartphone. -
 Yoti - your digital identityYoti is a digital identity application that provides users with a safe and efficient way to prove their identity and age. This app is designed for both Android devices and can be downloaded easily for those looking to manage their personal information securely. Yoti allows you to create a digital ID that can be used to interact with various businesses and individuals without the need to share excessive personal data.To get started with Yoti, users first need to add a
Yoti - your digital identityYoti is a digital identity application that provides users with a safe and efficient way to prove their identity and age. This app is designed for both Android devices and can be downloaded easily for those looking to manage their personal information securely. Yoti allows you to create a digital ID that can be used to interact with various businesses and individuals without the need to share excessive personal data.To get started with Yoti, users first need to add a -
 LifeLock Identity by NortonIdentity Theft Protection is hard. We make it easy for you with the LIFELOCK IDENTITY app and a NORTON 360 or LIFELOCK plan. You\xe2\x80\x99re across town\xe2\x80\x94and someone is taking out a bank loan in your name. We\xe2\x80\x99ll send you an identity alert\xe2\x80\xa0
LifeLock Identity by NortonIdentity Theft Protection is hard. We make it easy for you with the LIFELOCK IDENTITY app and a NORTON 360 or LIFELOCK plan. You\xe2\x80\x99re across town\xe2\x80\x94and someone is taking out a bank loan in your name. We\xe2\x80\x99ll send you an identity alert\xe2\x80\xa0 -
 Rain lashed against my office window as the clock ticked past midnight, the kind of storm that makes you question life choices. There I was - staring at a pixelated passport scan that looked like it'd been photographed through a jar of Vaseline. My biggest client's onboarding hung in the balance, and legacy verification systems were actively sabotaging me. Every failed upload felt like pouring salt into an open wound. That's when I remembered the new tool our CTO had raved about - some AI-powere
Rain lashed against my office window as the clock ticked past midnight, the kind of storm that makes you question life choices. There I was - staring at a pixelated passport scan that looked like it'd been photographed through a jar of Vaseline. My biggest client's onboarding hung in the balance, and legacy verification systems were actively sabotaging me. Every failed upload felt like pouring salt into an open wound. That's when I remembered the new tool our CTO had raved about - some AI-powere
